Managing web server security is a critical aspect of maintaining a safe and efficient online presence. One effective method to enhance security is by controlling access based on geographic locations. Plesk, a powerful web hosting control panel, offers a robust solution for this through its Firewall extension. Whether you need to block specific countries to mitigate security threats or whitelist certain regions to ensure access for your target audience, Plesk's Firewall extension provides the necessary tools.
In this tutorial, we will guide you through the process of blocking or whitelisting countries in Plesk using the Firewall extension. We'll cover the essential steps from installation to configuration, ensuring you have a comprehensive understanding of how to leverage this feature to enhance your server's security. By the end of this tutorial, you'll be able to manage access to your server based on geographic locations effectively, providing an additional layer of protection against unauthorized access and potential cyber threats.
When to Block an Entire Country
Blocking an entire country from accessing your server might seem drastic, but there are several scenarios where it becomes a necessary security measure:
-
Mitigating Cyber Attacks: If your server is experiencing frequent cyber attacks, such as Distributed Denial of Service (DDoS) attacks, brute force attempts, or hacking efforts from specific regions, blocking those countries can significantly reduce the threat.
-
Compliance with Regulations: Certain regulations or legal requirements may necessitate restricting access from specific countries. For instance, businesses dealing with sensitive data might need to comply with local data protection laws that restrict access from certain regions.
-
Reducing Spam: If your website or email server is bombarded with spam or malicious traffic originating predominantly from a specific country, blocking that country can help mitigate these issues.
-
Content Control: Some businesses may want to control the distribution of their content due to licensing agreements, ensuring that it is only accessible in authorized regions.
-
Bandwidth Management: If a significant amount of your server's bandwidth is consumed by traffic from certain countries that do not contribute to your business goals, blocking these countries can help optimize resource usage.
What Happens Under the Hood
When you block an entire country using the Plesk Firewall extension, several technical actions occur:
-
GeoIP Lookup: The Firewall uses a GeoIP database to identify the geographic location of incoming IP addresses. GeoIP databases map IP address ranges to specific countries.
-
Rule Creation: The Firewall creates specific rules that correspond to the identified IP address ranges for the targeted country. These rules are then integrated into the firewall's rule set.
-
Packet Filtering: When an incoming connection request is made, the firewall checks the source IP address against its rules. If the IP address belongs to a blocked country, the firewall immediately denies the connection request.
-
Logging and Monitoring: The firewall logs blocked connection attempts, allowing administrators to monitor and analyze the traffic patterns and potential threats.
-
Performance Impact: Modern firewalls, including Plesk's, are designed to handle large rule sets efficiently. However, extensive blocking rules can add some overhead to the firewall's processing. It's crucial to monitor performance and ensure that the firewall's rule set is optimized.
How to Identify If Your Server Is Being Abused from a Specific Country
To effectively block or whitelist countries, it's crucial to identify where abusive traffic is coming from. Here are several methods to determine if your server is being abused by a specific country:
Analyzing Server Logs:
- Access Logs: Review your web server’s access logs (e.g., Apache or Nginx logs) to see where traffic is originating. These logs typically contain the IP address of each request.
- Error Logs: Check the error logs for frequent failed login attempts, suspicious requests, or errors that indicate abuse.
Using Plesk’s Log Browser:
Plesk provides a built-in Log Browser that can help you inspect various logs directly from the Plesk interface. Navigate to Websites & Domains > Logs to view access and error logs.
Web Analytics Tools:
- Google Analytics: Set up Google Analytics for your website to get detailed reports on traffic sources, including geographic data.
- AWStats or Webalizer: These tools can provide detailed traffic analysis and help you identify unusual spikes in traffic from specific countries.
Firewall and Security Tools:
- Plesk Firewall Logs: Check the logs and alerts generated by the Plesk Firewall extension. It can provide insights into blocked attempts and the origin of these attempts.
- Fail2Ban: If you have Fail2Ban installed, review its logs to see which IPs have been banned and their geographic locations.
When to Whitelist an Entire Country
While blocking access from certain countries can enhance security, there are also scenarios where you might want to whitelist an entire country to ensure seamless access for legitimate users. Here are some situations where whitelisting a country is necessary:
Target Audience:
- Localized Services: If your website or online service is specifically targeted at users from a particular country, ensuring uninterrupted access for those users is crucial.
- Regional Promotions: When running promotions, events, or services that are exclusive to a certain country, whitelisting can help ensure that users from that country can access your site without interruption.
Business Operations:
- Remote Work: Companies with remote employees or partners in specific countries might need to ensure these users have consistent access to internal systems and resources.
- Country-Specific Partners: Businesses that work closely with partners, clients, or suppliers in a particular country may need to whitelist that country to avoid any disruptions in communication or service delivery.
E-commerce and Transactions:
- Localized Payment Gateways: For e-commerce websites that utilize local payment gateways or services, ensuring uninterrupted access to these services is essential for smooth transaction processing.
- Customer Trust: Ensuring that customers from a specific country can always access your e-commerce site can enhance trust and improve the customer experience.
Government and Regulatory Compliance:
- Compliance Requirements: Some regulatory requirements may mandate that access from specific countries must not be blocked, especially if the business operations are regulated by local laws.
- Avoiding Legal Issues: To avoid potential legal complications, businesses might need to ensure that they do not inadvertently block access from countries where they have legal obligations.
Installing the Plesk Firewall Extension
Log into your Plesk control panel and go to the "Extensions" menu. Here, search for "Firewall".
Select it, and if it hasn't been installed yet, click on the "Get it Free" button.
After installing the extension, you will be able to access it from "Extensions -> "My Extensions" or from "Tools & settings" -> "Security" -> "Firewall".
Block countries in Plesk
Open the Firewall extension. You will see a list of default rules. If the "Firewall protection" option is disabled, enable it.
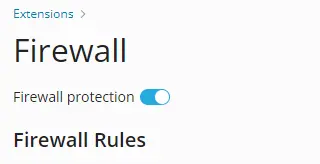
If you want to block a specific country, you need to create a new rule. To do this, click the + button.
Let's say we want to block Algeria and Albania. I'm using these countries as example, got nothing against them :)
The settings for the new rule should look like this:
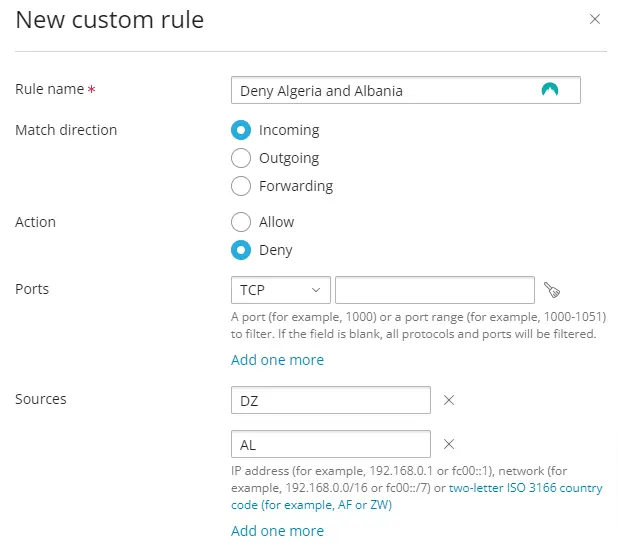
The "Rule name" can be anything. This is the name you give to the firewall rule. It should be descriptive enough to understand the purpose of the rule at a glance.
The "Match direction" setting defines the direction of the traffic that the rule will apply to.
- Incoming: Rules that apply to incoming traffic from external sources to your server.
- Outgoing: Rules that apply to outgoing traffic from your server to external destinations.
- Forwarding: Rules that apply to traffic passing through the server, used mainly for servers acting as routers or gateways.
The "Action" defines what action the firewall should take when traffic matches the rule.
- Allow: Permit the traffic.
- Deny: Block the traffic.
The "Ports" setting specifies the network ports the rule applies to. Ports can be defined for both TCP (Transmission Control Protocol) and UDP (User Datagram Protocol).
- TCP: Use this for connection-oriented protocols where reliable communication is required (e.g., HTTP, HTTPS, SSH).
- UDP: Use this for connectionless protocols where speed is prioritized over reliability (e.g., DNS, streaming services).
- Example: To block HTTP and HTTPS traffic from a country, specify ports 80 (HTTP) and 443 (HTTPS).
The "Sources" defines the source of the traffic the rule will apply to. This can include IP addresses, IP ranges, or ISO 3166 country code.
Example Configuration for Blocking a Country
To illustrate how these settings come together, let’s create a rule to block incoming traffic from China:
- Rule Name: Block China Traffic
- Match Direction: Incoming
- Action: Deny
- Ports: All ports (leave unspecified if you want to block all traffic, or specify particular ports such as 80 and 443 for web traffic)
- Sources: China (selected via GeoIP)
Example Configuration for Whitelisting a Country
Now, let’s create a rule to allow incoming traffic from the United States:
- Rule Name: Allow US Traffic
- Match Direction: Incoming
- Action: Allow
- Ports: All ports (or specify particular ports based on your needs)
- Sources: United States (selected via GeoIP)
Checking if the Firewall Rule is Working
After setting up your firewall rules in Plesk, it's important to verify that they are functioning as intended. One effective way to test these rules is by using a VPN service like NordVPN. By connecting to a VPN server in the country you have blocked or whitelisted, you can simulate access from that location and ensure the rule is correctly allowing or denying traffic.
NordVPN's extensive network of servers around the globe makes it easy to switch between different countries and test your firewall configurations comprehensively. Using NordVPN not only provides a secure way to verify your settings but also supports the continuous monitoring and tweaking of your server's security policies.
Consider using NordVPN to efficiently manage and test your firewall rules, ensuring your server remains secure and accessible as per your configured settings.